1. Short Description
In the framework of 7SHIELD, a set of tools will be offered to end-users, in order to support CI owners and operators, their security managers and risk management teams, assess their infrastructure against cyber-physical risks, identify their vulnerabilities and take appropriate decisions on security measures that will enhance their preparedness against potential incidents. This set of tools consists of:
- the CIRP-RAT, that will focus on natural, man-made and technological threats, and
- the DiVA tool that will focus on cyber threat assessment
This manual focuses on the CIRP-RAT tool, designed to estimate risk following a systematic procedure that incorporates, among other steps: threat identification, asset identification, scenarios definition, vulnerability assessment and consequences assessment. Risk is related mainly to three variables according to the following formula:
Risk = (Likelihood) x (Consequences), where Likelihood = (Threat) x (Vulnerability)
Risk = Threat x Vulnerability x Consequence (1
2. Main Purpose and Benefits
The
CIRP-RAT, is a web-based tool, offering through a user-friendly interface the
capability to conduct several what-if scenarios (assessments), in order to
calculate the risk. It is a question-driven approach, based mainly on threat
characteristics, the vulnerability of the assets, security measures in place
and impact analysis leading to the risk identification and measurement.
The tool
can be used and adapted to each 7SHIELD CI’s characteristics, assets, measures
and needs, so that each end-user can easily repeat the risk assessment
procedure, concluding with a detailed risk assessment report, assess what-if
scenarios and evaluate potential decisions of the management on security
measures. This way the end user will be able to identify the risks that are acceptable
(for which no or some additional security measures need to be implemented) or
unacceptable (for which new security measures should be implemented or the
already established should be updated/enhanced) for the CI.
Through the combination of CIRP-RAT with the DiVA tool, the user will be
able to conduct a holistic risk assessment of the CI, identifying the most
important cyber-physical risks and vulnerabilities.
In
general, the benefits offered to the end-user through CIRP-RAT are linked, but
are not limited, to the following aspects:
- Risk awareness and informed decision-making
on security measures
- Organized and holistic security
plan
- Improved allocation of
resources
- Preparedness
and anticipation of threats
- Incident
response capacity and mitigation of incident damage
3. Main Functions
The main function of the CIRP-RAT tool is that of calculating
the risk per threat and the overall risk of an infrastructure. The
methodological approach of CIRP-RAT is based on the following parameters:
- Threat identification and
scenarios definition
- Asset identification and
characterization
- Existing security measures
identification
- Impact identification
- Impact analysis
- Threat, Vulnerability and
Consequence analysis
- Risk estimation and
prioritization
- Risk evaluation &
mitigation
The main components of the tool regards
threat, assets’ vulnerabilities, security measures, impact and risk, as
described below in more detail.
Threat is defined as any indication, circumstance or event with the
potential to cause the loss of, or damage to, an asset or population. Threat is
summarized as the probability of the event to occur, as well as the level of
intensity.
Vulnerability is defined as a weakness of an asset that
could potentially be exploited by one or more threats. Vulnerability also
refers to the characteristics and circumstances of an asset that make it
susceptible to the damaging effects of a threat.
Measures to avoid and/or address existing and new threats and risks, categorized
in operational, procedureal, technical, etc.
Impact refers to the result and consequence that a threat would have on
the assets under study and can be categorised as Operational, Reputational,
Legal, Environmental, Financial, Societal.
Risk refers to the potential for loss, damage or destruction of an asset as a
result of a threat exploiting a vulnerability. Risk depends on the likelihood of the event occurring and consequences.
Following the
risk assessment, the risk index will be produced indicating to the user the
level of criticality for each respective threat, categorized as follows:
Figure 3.1 - Risk acceptance level
Based on the
above assessment and the comparative results for each scenario, the CI operator
will be able to identify the most important and necessary risk
mitigation/control measures that should be implemented, considering 4
high-level categories (Organizational, People, Physical, Technological).
4. Integration with other tools of 7SHIELD
As depicted in Figure 4.1- 7SHIELD contains
services used by the experts to prevent the threats associated with
cyber-physical attacks in the Satellite Ground Segment domain, covering the respective
macro-stage of crisis management, namely pre-crisis, like the risk assessment,
the resilience assessment, the analysis of the interdependencies and cascading
effects, and so on
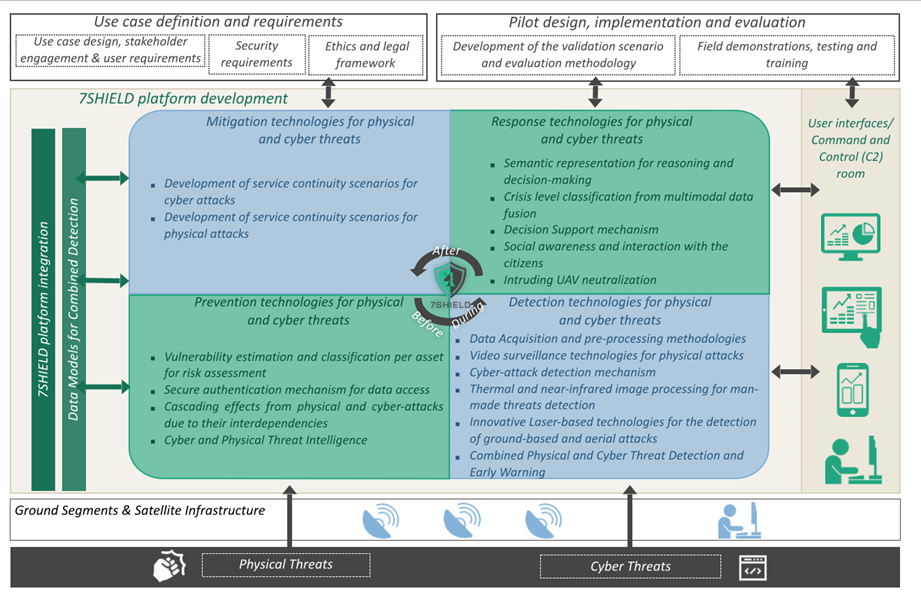
More specifically the risk
assessment framework, is related to the prevention and preparedness activities
(pre-crisis phase), providing support to the Ground Segment Operators through the
following tools:
- the Secure Authentication
Mechanism, i.e., the Single Sign On (SSO) technology developed by SERCO;
- the Model-Based Design and
Assessment (MBDA) tool, developed by RESIL;
- Risk assessment tools, composed
of the Critical Infrastructure Resilience Platform – Risk Assessment Tool (CIRP
- RAT) by STWS that is responsible for risk evaluation related to natural and
physical threats and by the Digital Vulnerability Assessment (DiVA) delivered
by ENG, responsible for the risk assessment of cyber threats;
- the Cyber and Physical Threat
Intelligence (CPTI) tool, developed by ENG.
The Single Sign On (SSO) provides
the authentication of 7SHIELD users. Once users are authenticated through the
7SHIELD SSO, they can access all the tools that are integrated with it.
The first element of the risk
assessment toolchain is the MBDA, and the user can access it after a successful
authentication through the 7SHIELD SSO. The MBDA has also the responsibility to
evaluate the cascading effects related to complex threats.
The Risk assessment tools receive
input from the MBDA model of a pilot. The CIRP-RAT is a platform that performs
the evaluation of the impact and severity of natural and physical threats on
the physical assets contained in the pilot model.
The DiVA evaluates the risk of
cyber threats and the impact on the cyber and also on the physical assets
included in the model, estimating a value connected to them.
Furthermore, the Cyber Physical
Threat Intelligence tool in the prevention phase gives an alert if there is a
probability that a hazardous event happens (both cyber and physical).
Finally,
the tools included in the framework (i.e., the MBDA, the CIRP-RAT and the DiVa)
are included in the 7SHIELD dashboard, i.e., in the CPTMD. This is to help the
operators to have all the tools reachable in a common environment and to have a
clear picture of the risk that a specific threat that is occurring can cause.
5. Infrastructure Requirements
The CIRP-RAT, is a web-based tool, deployed
as a Docker container (more information in section 6.1). The back-end services require at least 2 GB of RAM and a disk capacity of 20 GB, at least for the
first tests and demonstrations in the framework of the project.
6. Operational Manual
Figure 6‑2 – Log in through the SSO
authentication mechanism
In brief, the end-user should
initially configure the tool, based on CI’s internal information (e.g., assets
involved in the CI and respective vulnerabilities, threats of interest, security
measures in place, etc.). After or skipping this step, the user can begin with
the risk assessment, selecting the scenario to be analysed and defining the
respective threat (defining also probability and level of intensity). The
assets involved in the scenario will be selected, indicating the vulnerability
level for the specific scenario, followed by the efficiency level of security
measures in place for this scenario. Finally, an estimation of the impacts that
may be caused within the scenario under study, should be provided.
6.3.2 User Output
Following the above steps, the tool
will elaborate all the above information provided, leading to the risk
calculation. Repeating the above steps
for more scenarios will finally produce a concrete risk assessment report,
including several diagrams and prioritizing the risks, based on a risk index.
This way the end user will be able to identify the risks that are acceptable
(for which no or some additional security measures need to be implemented) or
unacceptable (for which new security measures should be implemented or the
already established should be updated/enhanced) for the CI.
7. User Interface
The functionalities provided by the
CIRP-RAT, are available to the users through a user-friendly graphical user
interface. Through that UI, users can be authenticated and design and execute
various what-if scenarios. Using these what-if scenarios, the CIRP-RAT will
calculate the risk indexes of the infrastructure on specific threats.
Initially, the user logs in (Figure
6‑2) to the
platform through an authentication mechanism (SSO), driving the user to the
main dashboard of the tool (Figure
7‑3). Due
to the user identification, information of the CI that (s)he belongs to is
presented in the upper part, while previous scenarios and assessments, along
with key results, are depicted in the history space.
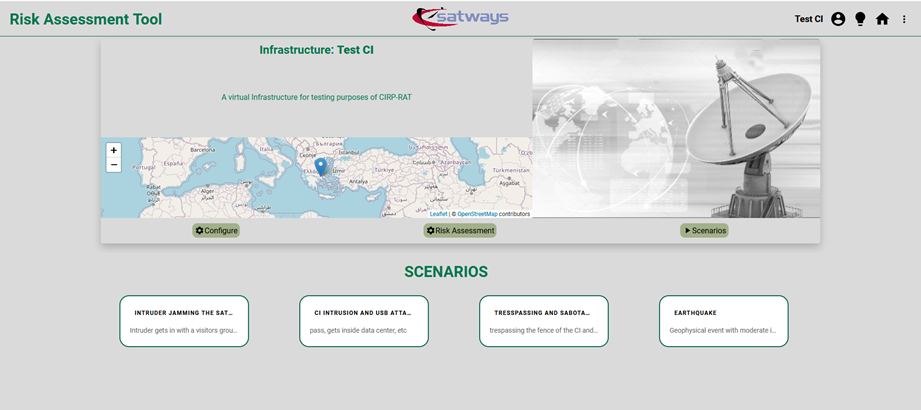
Figure 7‑3 - CIRP-RAT user's main dashboard
The first step that the user should
implement is of configuring the content of the platform, by clicking the  button, and adapting the parameters to the
specific CIs. This step can be repeated in case changes to the CI occur, e.g.,
after the implementation of new security measures, or the addition of new
assets.
button, and adapting the parameters to the
specific CIs. This step can be repeated in case changes to the CI occur, e.g.,
after the implementation of new security measures, or the addition of new
assets.
The next step indicates the
kick-off of the risk assessment process, by clicking the button  which is
related to threat identification and further analysis. When picking the new
risk assessment option, a new window that guides him/her through the process
pops-up, in order to define threat parameters, assets’ vulnerabilities,
security measures’ levels, etc.
which is
related to threat identification and further analysis. When picking the new
risk assessment option, a new window that guides him/her through the process
pops-up, in order to define threat parameters, assets’ vulnerabilities,
security measures’ levels, etc.
When all the above steps are
completed, the final step of the risk assessment process is activated. In this
last step, the user can see a summary of the values defined in the previous
steps and check if they are correct. If yes, the risk for the respective threat
is calculated and a set of results/diagrams is presented.
After
repeating the above steps, the user will be able to calculate the risk for
several threats of interest. When completing several risk assessments, then the
user is able to create a new scenario by clicking the  button, and then in the landing page click the new scenario button. This will correlate the data for several threats providing comperative results
through diagrams. Respective diagrams are created providing information on the scenario e.g. threat level, probability, assets’
vulnerability level, risk level, etc. as depicted in Figure 7‑4.
button, and then in the landing page click the new scenario button. This will correlate the data for several threats providing comperative results
through diagrams. Respective diagrams are created providing information on the scenario e.g. threat level, probability, assets’
vulnerability level, risk level, etc. as depicted in Figure 7‑4.
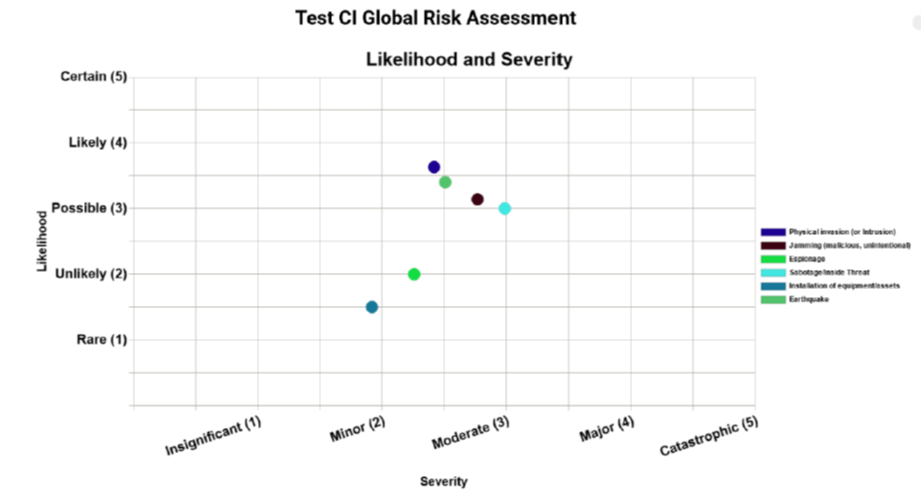
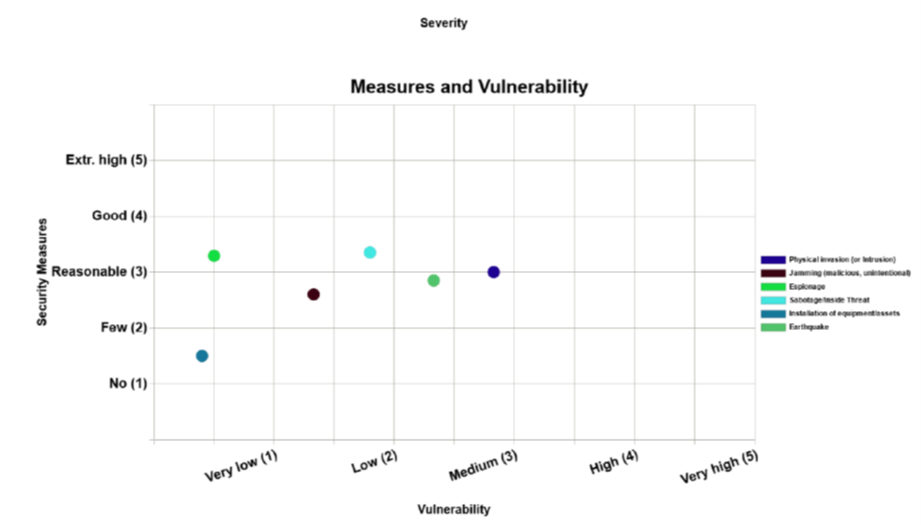
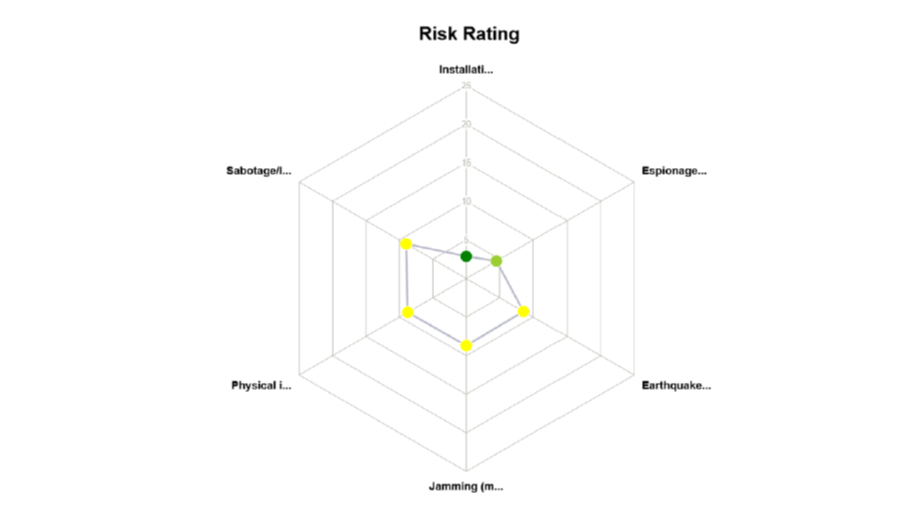
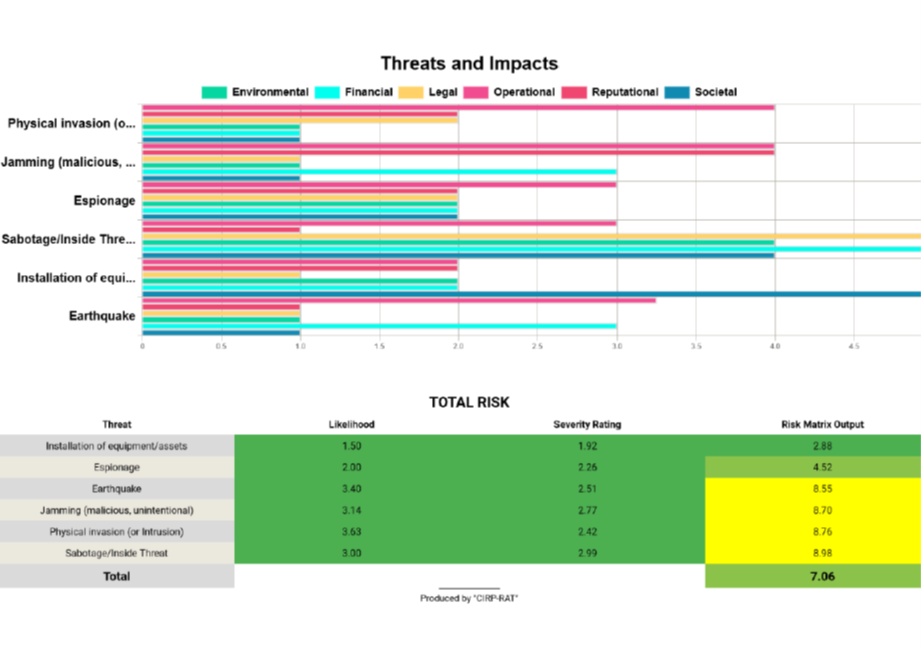
Figure 7‑4 – Scenario creation and overall assessment
The user is able to check on
previous scenarios through the history list depicted in the bottom left part of
the home screen (Figure
7‑3).