1. Short Description
The Crisis Classification (CRCL) module assesses
the severity level of an ongoing crisis event generated by a physical and/or
cyber-attack in Space Systems, ground Segments and Satellite data assets. A
multi-level fusion approach is applied which encompasses methodologies for the
processing of heterogeneous data generated by 7SHIELD detectors and
correlators. Specifically, the CRCL module receives aggregated (correlated) information
gained from the analysis of data that are captured by physical and cyber-attack
detectors, processes it and assesses the severity level of the C/P attack. At
the end, the crisis managers or the ground segment operators can receive
real-time updates on the severity level of the ongoing C/P attacks.
2. Main Purpose and Benefits
The main
goal of the Crisis Classification (CRCL) is to enhance the
decision-making processes, by providing real-time assessments of the severity
level of an ongoing physical and/or cyber-attack in critical satellite and ground
segments. To achieve this goal, it
encompasses methodologies for multi-level fusion in
Information and Decision level (Figure
2‑1). The
benefit of using the CRCL module is the real-time assessment of the severity
level of an ongoing P/C attack giving operators and crisis managers a better
picture of the current situation and helping them in their decision-making
process so as to respond to the crisis.
Particularly, at the Information
Fusion level, the real-time (or “near" real-time) information is analysed
by utilised machine learning techniques that are able to estimate the severity
level of a malicious event. The 7SHIELD detectors capture malicious C/P events
and generate heterogeneous data and alerts, which correlate from the 7SHIELD
correlators. Then, the situational picture is updated and can be considered as
the necessary input information to the CRCL module. Relied on this information,
the CRCL module can assess the severity level of the ongoing C/P attack at the
particular site. The exploitation
of the capabilities of Machine Learning approaches to “learn” from historical
data and fit the behaviour of the models according to the current situation
permits the development of a module that will be reliable and robust to assess
the severity level of a crisis in real-time.
Then, at the Decision Fusion level, the outcomes of the Information
Fusion level are enriched with information such as those that are stored in the
Knowledge Base, vulnerabilities of the assets that are exposed to C/P attacks,
or data for the availability of the sensors and hardware devices etc. At this
level, the CRCL module updates the severity level by employing a rule-based
approach.
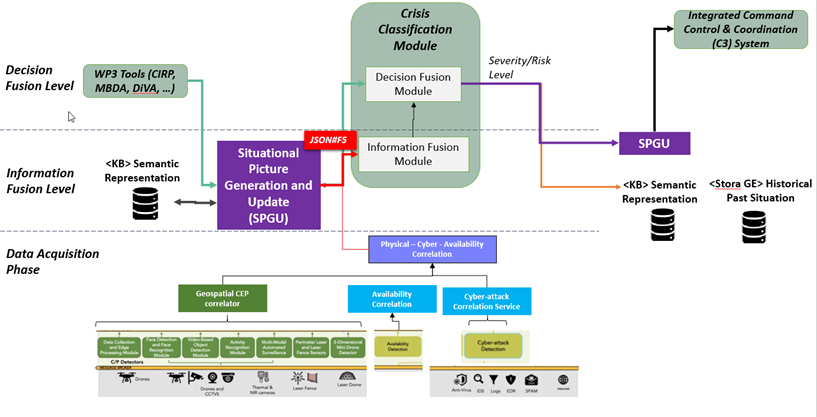
Figure 2‑1 - High-level architectural schema of Crisis
Classification
3. Main Functions
The main
functionality of the Crisis Classification module is the assessment of the
severity level of the ongoing C/P threat so as to update real-time the
situational picture of a ground segment. CRCL consists of two main components, namely the Information Fusion and the Decision Fusion.
The Information Fusion component collects aggregated data
generated from C/P events and estimates the severity level (Low, Moderate, High
or Extreme) by employing suitable trained machine learning models. Those models
have been trained based on historical C/P events. Hence, this process
demands the utilization of annotated datasets where each entry is formed by the
pre-defined event features and classified into one of the severity level's
categories.
Due to the nature of the problem that 7SHIELD presents, the uniqueness
of each space ground segment and the specific requirements, there is no
suitable open-source dataset that can efficiently be used to train the machine
learning algorithms of the Crisis Classification module. In order to overcome
that problem, we used Annotation Tool to effectively create our own annotated
dataset.
The Annotation Tool is a web-based application where an operator can
assess hypothetical attack scenarios in terms of its severity. A back-end
process (Scenario Builder) is responsible for the creation of random generated
attack scenarios. Those scenarios are stored into a database and retrieved for
annotation by end-users. The end-users can get access
into the application by providing their credentials (“Username” and
"Password”) (Figure
3‑1 (a)).
Then, the end-user can use drop-down lists in order to select the pilot site
and the event category of the hypothetical scenarios that will be generated for
annotation (Figure
3‑1 (b)).
After that, the main annotation page is displayed where the details for the
specific hypothetical attack scenario is presented and requested to the user to
annotate it in terms of the “Potential Consequences” and “Likelihood”. Based on user’s choices, the risk (severity level) of the attack is estimated
by a combination of the potential consequences and the likelihood of it.
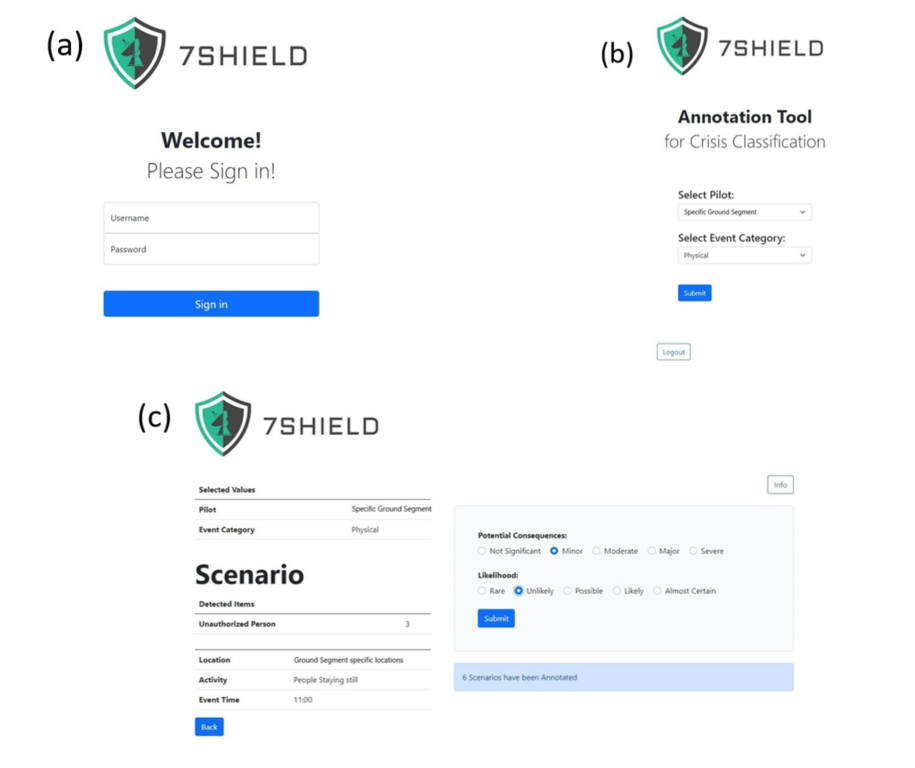
Figure 3‑1 – Annotation Tool UI: (a) Log-in page; (b) Pilot / Event
category selection page; (c) Main interface – Annotation page
The annotated datasets are used in order to train the machine learning
models. Various classifiers (Linear Regression, Support-Vector Machine,
Decision Trees, Random Forest and Gradient Boosting classifier) have been
tested over the annotated datasets and the best performance model in term of
the accuracy was chosen.
The Decision
Fusion component is a rule-based approach aiming to enrich the severity
level assessments. These rules are relied on the information concerning:
- the assets that are exposed to those attacks and their vulnerabilities
- the combination of the cyber and physical severity level assessments
that are provided in the previous level
- other specific rules provided by operators
- data for the availability of the sensors and hardware devices
4. Integrations with other Tools
The Crisis Classification (CRCL) is a back-end tool without having its own user interface. It is connected with the rest of 7SHIELD modules through Apache Kafka. The Crisis Classification gets all the correlated data in real-time through the Situational Picture Generation and Update module (SPGU). Then, it calculates the severity level of the current situation and its output is sent to SPGU, in order for the Integrated C3 System to be updated.
5. Infrastructure Requirements
CRCL is a
stand-alone application and it integrates in the 7SHIELD platform. Hence, no
specific infrastructure requirements are needed to install it.
6. Operation Manual
The CRCL module is packaged using
Docker in a virtual container along with its dependencies. It can run in any
Linux, Windows or macOS computer. In order to implement the tool in the main
7SHIELD platform, the user has to download the final version of the docker
container, build the docker in the system and then simply run it. All the
interconnections with the rest of the 7SHIELD modules are taken care
automatically in the back-end.
6.2 Getting started
As long as the CRCL is up and
running (through the virtual container that it is packaged), it is able to
consume every new event entry from the rest of the 7SHIELD platform, classify
its severity and communicate the output to the UI responsible 7SHIELD module,
in order for the end users to be able to notice it.
6.3 Nominal operations
6.3.1.
Notifications
The CRCL module is able to send
availability notifications in order to assure that the operation is nominal.
The data that the CRCL module needs
in order to assess the severity of an ongoing event are received through the
SPGU module in a custom format, through the kafka broker.
6.3.3 User Inputs
User inputs are not possible since
CRCL is a back-end tool.
6.3.4.
User output
The main output of the CRCL module,
the current severity of the ongoing event (or group of events) is communicated
to the users through the main 7SHIELD platform UI.
7. User Interface
Since the CRCL module is a back-end tool, there is no
user interface. It communicated with the end users through other modules
responsible for the UI.