A host can use another host, this
allows certain parameters to be defined in a general way. It is then sufficient
to configure the use parameter in the hosts using it.
Example with the generic-webservice
used by the previous host:
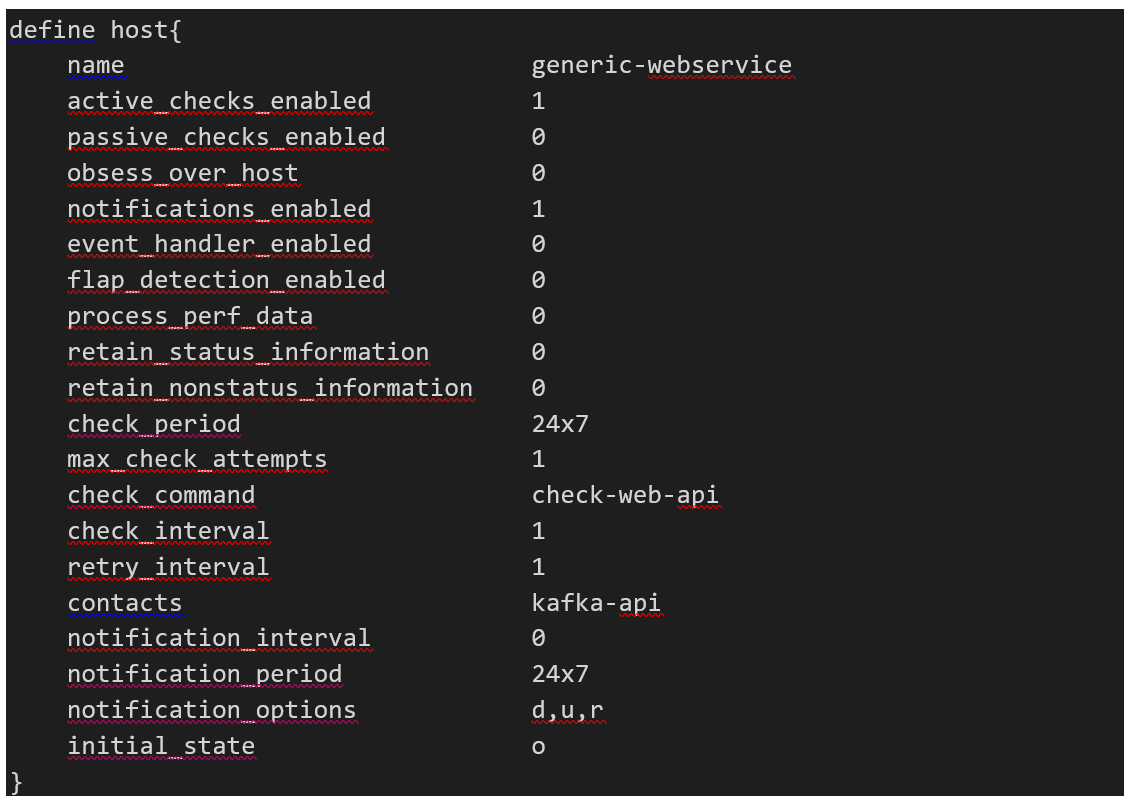
Lines explanation:
-
Active_checks_enabled: his directive is used to determine whether active checks (either
regularly scheduled or on-demand) of this host are enabled. Values: 0 = disable
active host checks, 1 = enable active host checks (default).
-
Passive_checks_enabled: This directive is used to determine whether passive checks are
enabled for this host. Values: 0 = disable passive host checks, 1 = enable
passive host checks (default).
-
Obsess_over_host: This directive
determines whether checks for the host will be "obsessed" overusing
the ochp_command.
-
Notifications_enabled: This directive is used to determine whether notifications for this
host are enabled. Values: 0 = disable host notifications, 1 = enable host
notifications.
-
Event_handler_enabled: This directive is used to determine whether the event handler for
this host is enabled. Values: 0 = disable host event handler, 1 = enable host
event handler.
-
Flap_detection_enabled: This directive is used to determine whether flap detection is
enabled for this host. More information on flap detection can be found here.
Values: 0 = disable host flap detection, 1 = enable host flap detection.
-
Process_perf_data: This directive is used to determine whether the processing of
performance data is enabled for this host. Values: 0 = disable performance data
processing, 1 = enable performance data processing.
-
Retain_status_information: This directive is used to determine whether status-related
information about the host is retained across program restarts. This is only useful
if you have enabled state retention using the retain_state_information
directive. Value: 0 = disable status information retention, 1 = enable status
information retention.
-
Retain_nonstatus_information: This directive is used to determine whether non-status information
about the host is retained across program restarts. This is only useful if you
have enabled state retention using the retain_state_information directive. Value: 0 = disable non-status information
retention, 1 = enable non-status information retention.
-
Check_period: This directive is used to
specify the short name of the time during which active checks of this host can
be made.
-
Max_check_attempts: his directive is used to define the number of times that Nagios
will retry the host check command if it returns any state other than an OK
state. Setting this value to 1 will cause ADM to generate an alert without
retrying the host check. Note: If you do not want to check the status of the
host, you must still set this to a minimum value of 1. To bypass the host
check, just leave the check_command option blank.
-
Check_command: This directive is used to specify the short name of the command
that should be used to check if the host is up or down. Typically, this command
would try and ping the host to see if it is "alive". The command must
return a status of OK (0) or ADM will assume the host is down. If you leave
this argument blank, the host will not be actively checked.
-
Check_interval: his directive is used to define the number of "time
units" between regularly scheduled checks of the host. Unless you've
changed the interval_length directive from the default value of 60, this number
will mean minutes.
-
Retry_interval: This directive
is used to define the number of "time units" to wait before scheduling
a re-check of the hosts. Hosts are rescheduled at the retry interval when they
have changed to a non-UP state. Once the host has been retried
max_check_attempts times without a change in its status, it will revert to
being scheduled at its "normal" rate as defined by the check_interval
value.
-
Contacts: This is a list of the short names of the contacts that should be
notified whenever there are problems (or recoveries) with this host. Multiple
contacts should be separated by commas.
-
Notification_interval: This directive is used to
define the number of "time units" to wait before re-notifying a
contact that this service is still down or unreachable. Unless you've changed
the interval_length directive from the default value of 60, this number will
mean minutes. If you set this value to 0, ADM will not re-notify contacts about
problems for this host - only one problem notification will be sent out.
-
Notification_period: This directive is used to specify the short name of the time
during which notifications of events for this host can be sent out to contacts.
If a host goes down, becomes unreachable, or recoveries during a time which is
not covered by the time, no notifications will be sent out.
-
Notification_options: This directive is used to
determine when notifications for the host should be sent out. Valid options are
a combination of one or more of the following: d = send notifications on a DOWN
state, u = send notifications on an UNREACHABLE state, r = send notifications
on recoveries (OK state), f = send notifications when the host starts and stops
flapping, and s = send notifications when scheduled downtime starts and ends.
If you specify n (none) as an option, no host notifications will be sent out.
-
Initial_state: By default, ADM will
assume that all hosts are in UP states when it starts. You can override the
initial state for a host by using this directive. Valid options are o = UP, d =
DOWN, and u = UNREACHABLE.