1. Short Description
Cyber and Physical Threat
Intelligence (CPTI) is a tool that allows you to search the web for threats
relating to the critical infrastructure to be protected.
In
particular, this search is carried out among the messages of the most used
social networks.
2. Main Purpose and Benefits
Goal of the Threat Intelligence
service is to allow searching, monitoring, and analyzing of threats across
multiple sources, including: Dark Web communities and marketplaces
(TOR-based); Underground communities and
marketplaces (Internet-based); Social media networks; Blogs, Forum etc.
3. Main Functions
Currently
the tool is limited because it is trained only for a certain number of keywords
to search and only one social network is supported: Twitter
3.1 Data Extraction
This is
the function suitable for extracting data from social networks, specifically:
Twitter. Through this feature it is possible to extract data and information
from tweets (messages) found on the net using specific criteria.
3.2 Orchestration
The orchestrator allows you to
route data to and from the component that has to manage and process it. In this way, messages are sent to
the Apache Kafka broker, communication between the Database and the data
analysis services is managed, data mapping is performed, etc.
3.3 AI Identification
The artificial intelligence-based
feature allows you to identify possible threats in social network messages.
3.4 HistoricizationEach message is persisted in a
database: requests, extracted data, alerts, etc..
4. Integration with other ToolsThe interaction of CPTI with the other tools of
the 7Shield framework is shown below.
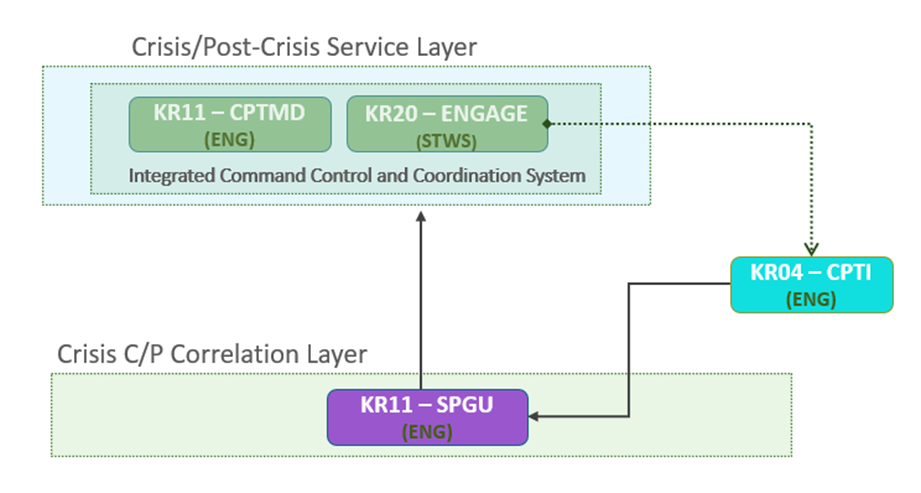 Figure 4 - CPTI inside 7Shield framework
Figure 4 - CPTI inside 7Shield framework
From the ENGAGE tool of STWS a search is
made for some keywords in the social network twitter.
When the similarity threshold is calculated
as greater than or equal to 0.4, the related message is considered as a threat.
A severity is then devised and among all the messages considered as a threat
the highest severity is chosen which will contribute to the updating of the
severity level of the Situational Picture managed by SPGU. SPGU will then also
send an update to ENGAGE and furthermore the STWS tool interface will show the
messages / threats found in the social network.
5. Infrastructure Requirements The
module is dockerized and can run on any system, virtualized or not.
A system with 16GB RAM and 100GB
HDD is definitely recommended.
In this
case having a larger virtual memory is necessary since the message processing
components of CPTI require a particular effort. The type of resources is
directly proportional to the performance of the tool which on average and with
these machine requirements, the tool takes an average of about 1 hour to
process data.
6. Operation Manual
For the first deployment, the basic
training data must be imported:
- docker
exec -it ti_mongo /bin/bash (first time)
- sh
/tmp/dump/tweets/import_tweets.sh
Then it must be opened on Apache
Ni-Fi browser:
http://7shield-spgu.eng.it:9001/nifi/
and follow the following steps:
- import TI_XXX.xml (NiFi
Template) from down/left Operate box.
- add template on the grid (from
top bar add template)
- config. Kafka consumer /
producer (passwords, certificates, bootstrap server)
- config. data extractor
(dbl-click -> for each yellow box (invoke http) set user/pass on for Anita)
by inserting the Anita credentials.
- go back and press play button
(from down/left Operate box)
7. User Interface
The user interface of CPTI is
ENGAGE by STWS.
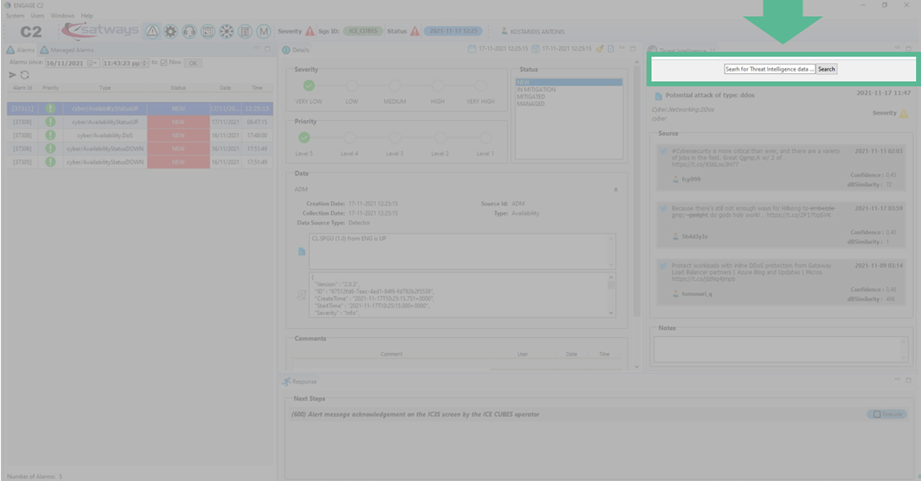
Figure 2 - ENGAGE: keyword search
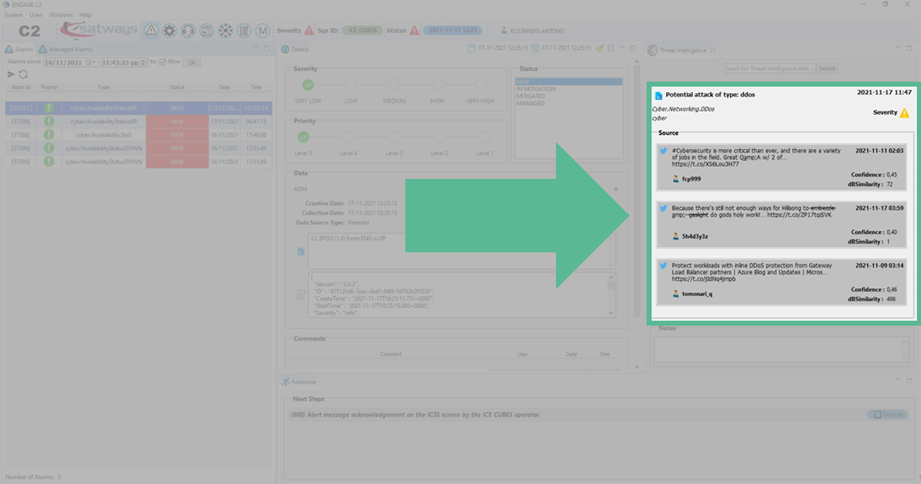
Figure 3 - ENGAGE: CPTI threats found